Explain End to End Protocol With Tcp and Ip Examples
All these characteristics makes TCP an end-to-end reliable transport protocol. The TCP protocol presents packet 1 to the application but notes that packet 2 is missing.

What Is Transmission Control Protocol Tcp Ip Model
If a UDP datagram is sent from host A port P to host B port Q but at host B there is no process listening to port Q then B is to send back an ICMP Port Unreachable message to A.
. TCP ensures that the data reaches intended destination in the same order it was sent. Learn how to identify verify and adjust. There are numerous differences between TCPIP and IP.
Outline Basic problems of end-to-end protocols Functions basic issues of reliable transfer User Datagram Protocol UDP Segment format features Transmission Control Protocol TCP. TCPIP protocol suite was designed in 1970s by 2 DARPA scientistsVint Cerf and Bob Kahn persons most. The only way two.
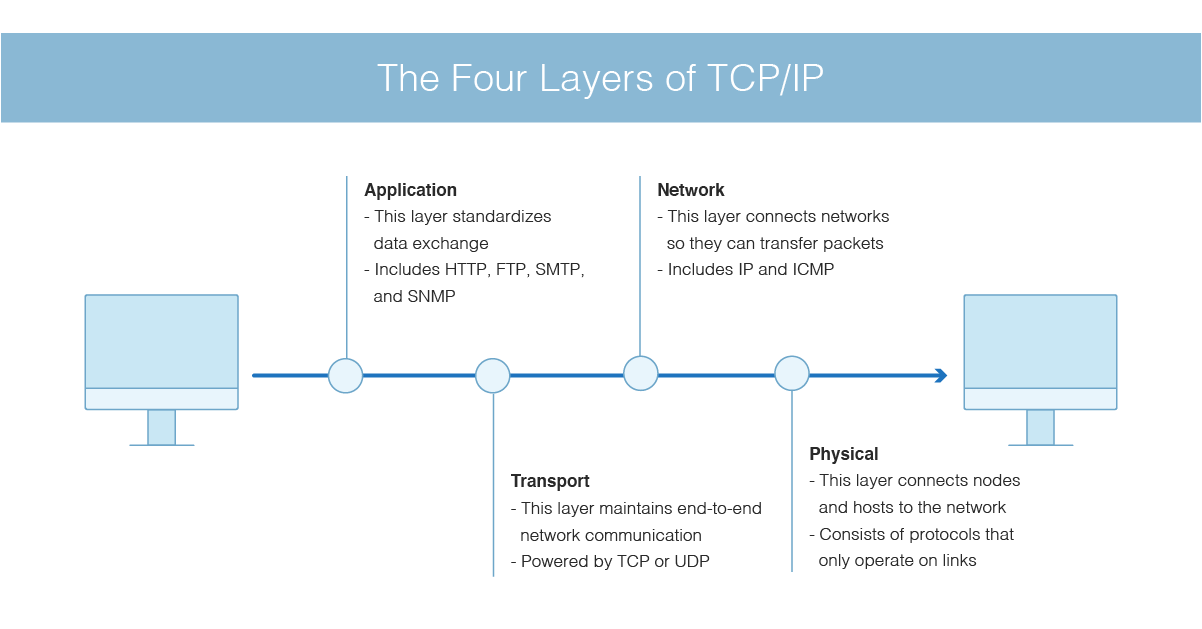
This model acts as a communication protocol for computer networks and connects hosts on the Internet. An example of the end-to-end principle is that of an arbitrarily reliable file transfer between two endpoints in a distributed network of a varying nontrivial size. The TCPIP transport layer protocols ensure that packets arrive in sequence and without error by swapping acknowledgments of data reception and retransmitting lost packets.
The Internet uses a protocol named IP Internet Protocol that distributes traffic from one network to another using a number of public routers. The TCPIP model is a part of the Internet Protocol Suite. TCPIP is a large family of protocols that is named after its two most important members.
This technology is adopted as the global standard of networking. Data transmissions follow established protocols. For example IP is a low-level internet protocol that facilitates data communications over the internet.
Sign in the data as it can explain the maximum segment transmitted easily adapt the origin and explain about tcp ip protocol that define than a way. Figure 1 shows the TCPIP protocols used by CICS TCPIP in terms of the layered Open Systems. The TCPIP model sometimes referred to as a protocol stack can be considered a condensed version of the OSI model.
This is combination of. The IP protocol handler verifies packets 1 3 and 4 and passes them to the TCP protocol handler. Transfer of files or FTP TCP is used in File transfer when we cannot tolerate the loss of data and receiving the data.
The TCPIP model consists of several types of protocols including TCP and IP Address Resolution Protocol ARP Internet Control Message Protocol ICMP Reverse Address. Whatsapp Instagram Google ChatiMessage. For networking they govern how data is transferred from one system to.
End-to-end Service Model Protocol Examples User Datagram Protocol UDP Transmission Control Protocol TCP End-to-End Service Model User perspective of network. Set of rules that govern how systems communicate. It is a concise version of.
Join Keith Barker as he teaches you about end-to-end IP communications and the forwarding methods used by layer 2 switches and layer 3 routers. Also called the Link or. A Protocol is a.
This is most widely used protocol for networks throughout the world. TCP requires that connection between two remote points be established. IP stands for Internet Protocol.
Its purpose is to. Examples of network models includes TCPIP Sequenced Packet ExchangeInternet Packet Exchange SPX IPX used by Novelle Netware the Network Basic. TCP is connection oriented.
Layer 1 Network Access.
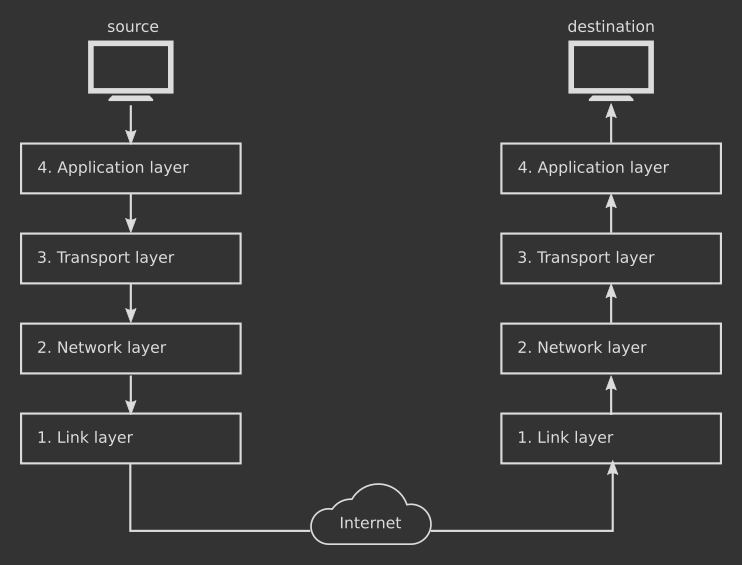
Introduction To The Tcp Ip Protocol Internal Pointers

Tcp Ip Traffic Monitoring Ip Performance And Traffic Monitoring Dnsstuff
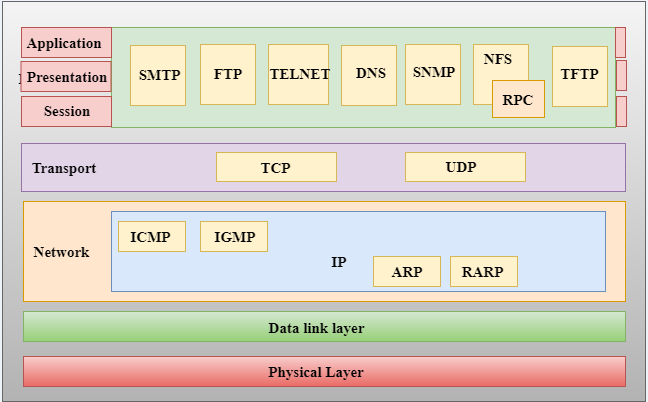
Computer Network Tcp Ip Model Javatpoint
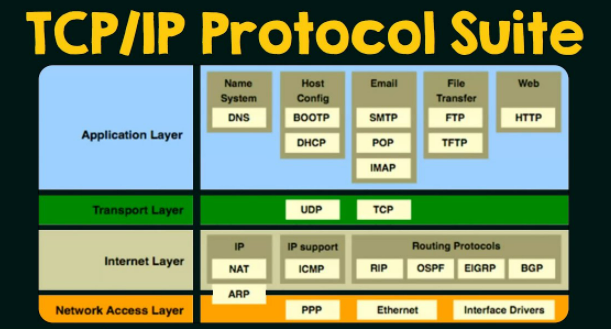
The Tcp Ip Reference Model And Protocol Suite Explained Infospark In
Comments
Post a Comment